It seems that the dark elves responsible for pumping out unwanted spam of all kinds have the Christmas spirit of giving right now. Unfortunately, they completely misunderstood the true meaning of the season and are bent on raking in money for themselves.
Whether it be email or Blogger referral spam, the filters have been tested to the breaking point in December. Earlier, I posted an update on seoairport suddenly returning with a flood. A new approach that I haven’t seen outside of emails showed up too and that’s what I’ll be covering in this post.
I hope by now that everyone knows not to open an Adobe Acrobat (PDF) attachment from a stranger when they get one in their inbox. This has been a way to deliver trojans and viruses onto PCs for many years.
So it was surprising to see referral spam that linked to PDFs including one hosted on Amazon’s cloud service which arrived as s3 . amazonaws . com / pdf-1ydO / qyR20YHDImN9.pdf on my Blogger stats page.
Why would anybody use such a discredited way to get hits? Another referral and a little digging provided me with a theory.
Remember to not click on links such as these, leave it to security pros and madmen to investigate. In my case, it is the latter though a virtual machine and an anonymous routing service were employed to keep my PC uncompromised.
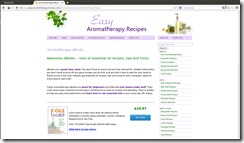

Easy Aromatherapy Recipes is the subject of initial PDF spam hawking ebooks compiling those recipes. The first thing I noticed was the huge link embedded in the PDF, which looked like a lower quality screen grab of a web page. The second thing was the old trick of stuffing keywords at the end in the hopes of getting ranked on Google.
Of course the link took me the web page, however the bottom half was completely different. Gone was the keyword stuffing and in its place were typical sales guarantees.
Kaley Zimmerman is person behind the site and shows up as being from Ontario, Canada. Further looking around the Net shows she has multiple pages up on aroma therapy, a form of quack medicine that relies heavily on placebo effect.
Besides the obvious making money from selling ebooks, she gets money from affiliates when people buy from clicking on a link from her site. This is a common and legitimate way of making money or supporting the costs of a website. Remember this when reading through the next spam that arrived.
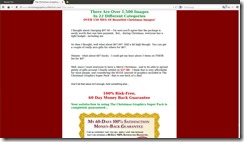
If you were wondering why I titled this post Spam for Christmas, origin . library . constantcontact . com / download / get / file / 1119162503061-2645/500439.pdf is what inspired it. Featuring the same layout as the previous PDF, it too is stuffed to the gills with keywords.
A cheaply thrown together page is reached through the hyperlink which shows cheaply thrown together packaging of cheaply thrown together public domain Christmas artwork for sale. Basically, they want you to buy graphics you could find for free on the Web.
I suspected that Victorian era art would be involved, since copyrights have expired long ago. Scrolling down revealed that surmise to be accurate.
Quite a deal, 150 megabytes of images for the lowly cost of $27. That’s not even enough to fill a CD-ROM!
Aside from the hard sell for art at a terrible price, another detail caught my eye. ClickBank is the host for the site and while being a real virtual storefront firm, it gave me a piece of the puzzle I was missing.
Again with affiliate sales, this time offering half the money if someone buys from an ad on your blog or page for the site. This is the kind of thing ripe for abuse by third parties running wild with setting up ads all over the place.
In fact, the referral spam may not have originated with the sites in the first place, though it is likely. No matter the case, I still would like to give a virtual lump of coal to both sites this Christmas.
Exploiting holidays in shady ways to make money is not something I approve of and that goes doubly so for Christmas spam!











No comments:
Post a Comment
Please keep all comments clean, respectful to other commenters, and use full links if you include one. No shortened links or profanity will be allowed. Thank you!